I learned PAO mnemonic technique for remembering long numbers based on assignation each digit combination 00-00-00 — 99-99-99 a fixed image and realized that I already have strong associations beetween alphabet symbols and Angband monsters. Hence I can remember a relatively short senseless various-case chars combination like "SeJffGoZq" trough creating a mental visual story about a spider, floating eye, snake, tigers etc.. You put more work to remember something that way in comparsion with rote memorization, but such memories tend to fade slow over time even without repetition.
A way to remember good passwords
Collapse
X
-
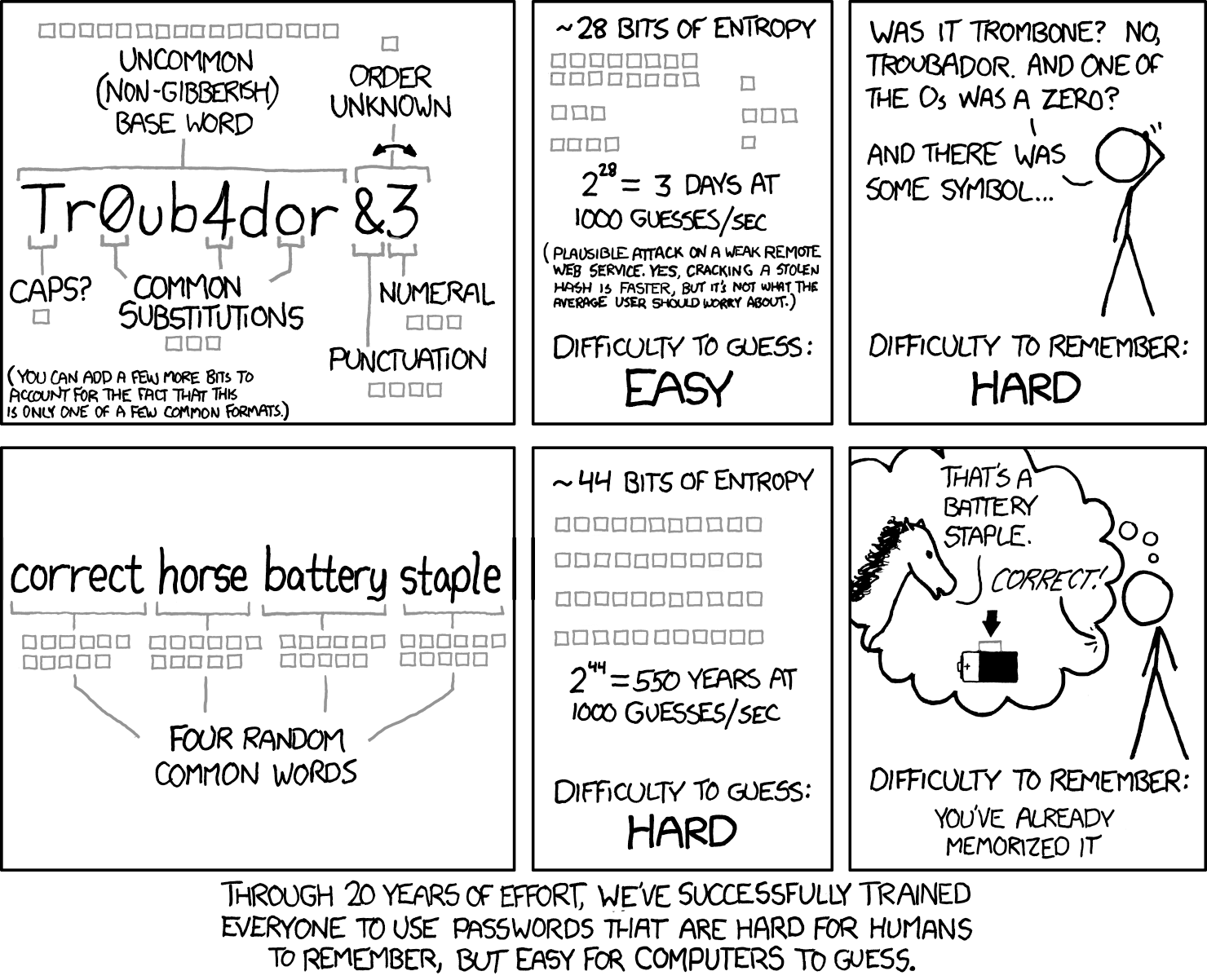
I think passwords consisting of several words or a phrase are generally more secure than short, complex, and hard to remember passwords.
Considering a password field which only allows lower case and uppercase letters, "SeJffGoZq" (max 52^9 attempts) is less secure against brute-forcing methods than a password such as "sunnydayvisibility" (max 52^18)- even if the password length is somehow known and the program attempts lower case letters first. The latter password is probably easier to remember even with this mnemonic.
Using roguelike character sets to remember nonsense strings of letters is a good idea, but I think there are better applications than passwords! -
Apparently this isn't quite as good a method as it used to be, but it's quite easy to remember hard to brute force passwords in this format.
On the other hand, common inscriptions should be relatively straightforward to remember, and you can put arcane hints if there are questions related to the password.
"Keleks" = @m9!d!k!vComment
-
Use a password manager?
I like kpcli myself, since it's text-based and compatible with KeePass database formats:
Comment
-
Here's the current recommendation from experts: Generate[1] separate passwords for each site and write them down. Obviously you shouldn't keep those written-down password on a post-it on your monitor[2], but perhaps in your wallet or just as an encrypted file on your hard drive.
EDIT: I suppose I should explain a little bit of the reasoning. Point #1: Some random person stealing your wallet is most likely not interested in your twitter password. They're interested in your money and/or credit cards. Point #2: Using the same password across different sites is a really bad idea because once a valid username/password combination has been obtained, it's completely trivial to compromise a lot of different sites in an automated fashion. (That is to say: The fact that it would take a human X amount of time to compromise your Twitter, Instagram, Facebook, Gmail, etc. means nothing when a computer program can do that in a few seconds given that the correct username/password combination is known.)
[1] That is, use, e.g. apg, to generate a separate password. (If you're paranoid you might want to tweak the parameters to apg, though.) Actually, if it's a site you don't particularly care about you might want to also use apg to generate the "user name", though usually sites will just want a working e-mail.
[2] See http://arstechnica.com/security/2015...-tv-interview/ for how well that can go...Last edited by AnonymousHero; October 22, 2016, 20:57.Comment
-
Using just one word plus maybe some numbers and/or basic transformations (like replacing "o" with 0) leaves you with a "weak" password that can relatively rapidly be guessed by an attacker who is both willing and able to brute-force-attack you. However, adding just one more word to the password greatly increases the number of potential combinations the attacker would have to try, and a three-word password has frankly amazing strength compared to what people actually commonly use these days.
Such attacks are somewhat rare these days; usually the infrastructure of the site itself is attacked and the passwords[1] get exposed and then re-used on other sites. Still, you shouldn't make your passwords easy to guess. Use a password manager, or write the passwords down. The important thing is that an attacker that gets one of your passwords should not be able to figure out what your password is on a different site -- so if your password was "applesandbananas1" on this site, for example, an attacker that hacks the site might plausibly guess that your password is "applesandbananas2" (or 3, 4, etc.) on another site.
[1] Stored, depressingly, in plaintext in their database, because people are Bad At Security. Passwords ought to be stored as a "hash", which is a consistent one-way mathematical transformation, because all you care about is if the value the user input matches the value stored in the database. Hash the input, and if it matches the hash in the database, all is well. There is zero reason to store the actual password, and it greatly increases the damage from a hack. An attacker that gets their hands on the hash will, if you do it properly, have great difficulty recovering the passwords from the hashes.Comment
-
@Derakon
Nice comment. Just a little addendum: Of course the usual corporate "Best Practice" (ugh!) strategy is to force people to choose a new password every few months... and what you get is "mypassword1" changes to "mypassword2", changes to "mypassword3" (or the moral equivalent -- these things are usually ridiculously easy to game). Sigh.
EDIT: Small addendum for anyone who's interested in the technology: In addition to just "hashing" you'll also want to add a salt to avoid attacks on one of your users becoming an attack on all your users. (Dundundun!). (Read the wiki page for details.)Last edited by AnonymousHero; October 22, 2016, 21:36.Comment
-
That's incredible!I learned PAO mnemonic technique for remembering long numbers based on assignation each digit combination 00-00-00 — 99-99-99 a fixed image and realized that I already have strong associations beetween alphabet symbols and Angband monsters. Hence I can remember a relatively short senseless various-case chars combination like "SeJffGoZq" trough creating a mental visual story about a spider, floating eye, snake, tigers etc.. You put more work to remember something that way in comparsion with rote memorization, but such memories tend to fade slow over time even without repetition.Comment

Comment